CVE-2025-50454: Blue Access Cobalt X1 Authentication Bypass
Affected Versions
<=02.000.187
Remediated Version
02.000.195
Introduction
I recently came across an interesting authentication bypass vulnerability in some vendor software that controls badge-accessed door locks in commercial buildings. The software is called Cobalt X1, created by the vendor Blue Access. The discovery of this vulnerability came as a result of a sanctioned penetration test I was performing. I was able to exploit the vulnerability, which resulted in full administrative access to the application, effectively controlling all doors and employee badge access to this specific building.
Technical Details
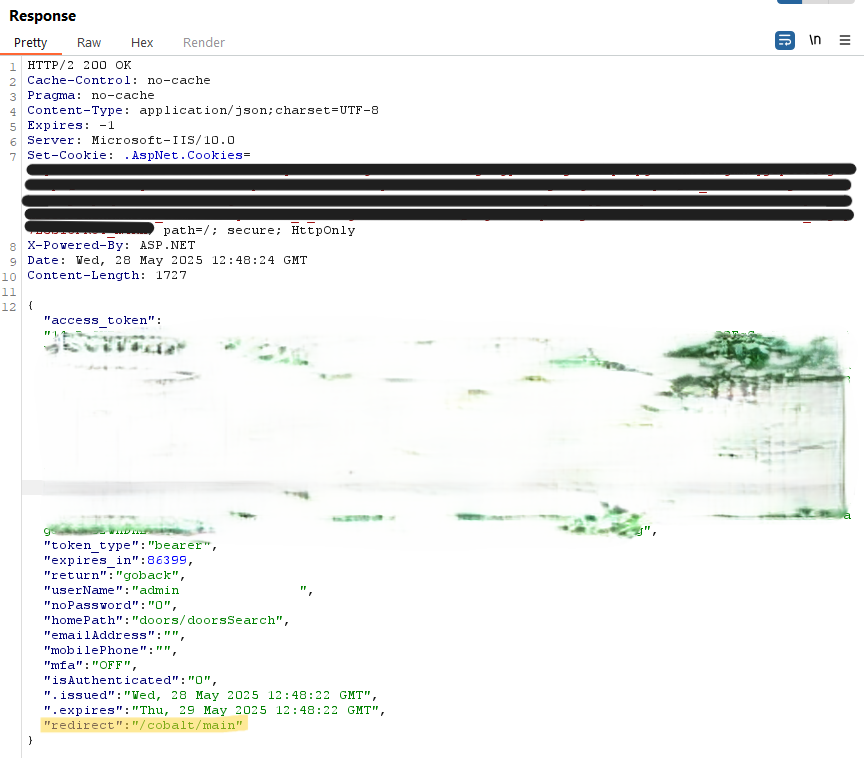
When presented with a login page during a pentest, I typically begin as anyone would, with attempting to login using common credentials. Even when mostly unsuccessful, I can still observe the login behavior and potentially enumerate more information during this process. When observing the http response for the invalid login attempt, I noticed that it contained a bearer token in the body, which showed the “userName” property as “admin”, the username I had entered. I then attempted to access the “redirect” url in the token: ‘/cobalt/main’. I was now on the main dashboard of the Cobalt X1 application, logged in as “admin”. Looking at the token response from my initial invalid login, this is indeed a valid token for the admin user account. However, without force browsing to the dashboard url, this would simply go unnoticed.
Redacted login POST response:
Attacker Value
When thinking about physical security, I think of security guards, RFID badges, and revolving doors. What I don’t think about is all of that being bypassed by a poor authentication implementation in a vendor’s badge access software. This exploit, while easily identified, poses pretty detrimental consequences in the wrong hands. (Think removing all employee badge access and completely locking down a hospital in exchange for a ransom…) I don’t know the extent to which this software is widely used, but I know for the implementations I was testing, it could easily have similarly awful consequences.
Disclosure
This vulnerability was disclosed to Blue Access, who immediately released a remediated patch in version 02.000.195.